 Many manufacturers rely on system integrators to design and install compliant machinery safety solutions, but they often struggle to find the most capable provider. To help ease that process, Rockwell Automation continues to expand its global Machinery Safety System Integrator program. Three new members have joined in the first half of 2016, bringing the total number to 26.
Many manufacturers rely on system integrators to design and install compliant machinery safety solutions, but they often struggle to find the most capable provider. To help ease that process, Rockwell Automation continues to expand its global Machinery Safety System Integrator program. Three new members have joined in the first half of 2016, bringing the total number to 26.
“We created this program in 2014 to connect manufacturers with safety system integrators they can trust,” said Mark Eitzman, manager of safety market development, Rockwell Automation. “It’s become a valuable resource for manufacturers because we do the vetting for them. We make sure the integrators thoroughly understand current safety standards and know how to apply safety technologies in a way that also improves plant productivity.”
To be eligible, candidates must be current Rockwell Automation Solution Partners or Recognized System Integrators with three to five years of machine safety experience. They must complete an intensive education and assessment process, but Rockwell Automation also recognizes third-party certification from industry-accepted organizations, such as TÜV or exida.
After meeting these initial requirements, each candidate’s safety engineers complete training modules on topics such as global safety standards, safety risk assessment practices, and safeguarding mitigation and validation. Finally, each candidate must submit a machinery safety project that is consistent with global standards.
The three new members of the program include:
- Automation Electronics Group and Systems (AEG Systems), a Rockwell Automation Recognized System Integrator based in Mexico, specializes in customized process, motion and MES applications for clients around the world.
- RT Engineering, a Rockwell Automation Recognized System Integrator located in Franklin, Massachusetts, provides custom controls and automation solutions for customers in the medical, pharmaceutical and metals industries.
- SINCI, a Rockwell Automation Solution Partner located in Guadalajara, Mexico, specializes in control, process and information applications for customers in food and beverage, metals, mining and utilities.

 Mike Medoff, exida senior safety engineer presented the 2015 exida Safety Award in the Cybersecurity Category to Schneider Electric recognizing their Process Automation Cybersecurity Development Process. The presentation was delivered at Connect 2016, Schneider Electric’s Automation Conference on May 24, 2016 in New Orleans, LA.
Mike Medoff, exida senior safety engineer presented the 2015 exida Safety Award in the Cybersecurity Category to Schneider Electric recognizing their Process Automation Cybersecurity Development Process. The presentation was delivered at Connect 2016, Schneider Electric’s Automation Conference on May 24, 2016 in New Orleans, LA.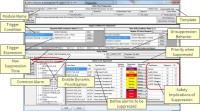 The ISA-18.2 and IEC 62682 alarm management standards provide recommended targets for average alarm rate and for alarm floods - a condition during which the alarm rate is greater than the operator can effectively manage (e.g., more than 10 alarm per 10 mins) Ref ISA-18.2. During alarm floods the chance of an operator missing an alarm or making a mistake is increased. The following table taken from IEC 61511 shows how the reliability of humans is impacted by stress.
The ISA-18.2 and IEC 62682 alarm management standards provide recommended targets for average alarm rate and for alarm floods - a condition during which the alarm rate is greater than the operator can effectively manage (e.g., more than 10 alarm per 10 mins) Ref ISA-18.2. During alarm floods the chance of an operator missing an alarm or making a mistake is increased. The following table taken from IEC 61511 shows how the reliability of humans is impacted by stress. exida, the global leader in functional safety and cybersecurity certification for the process industries has certified three Schneider Electric product development sites in Foxboro, Mass., Worthing, U.K., and Hyderabad, India, for compliance with the exida Security Development Lifecycle certification based on IEC 62443-4-1. exida is a globally recognized ISO 17065 accredited Certification Body (CB) in cybersecurity.
exida, the global leader in functional safety and cybersecurity certification for the process industries has certified three Schneider Electric product development sites in Foxboro, Mass., Worthing, U.K., and Hyderabad, India, for compliance with the exida Security Development Lifecycle certification based on IEC 62443-4-1. exida is a globally recognized ISO 17065 accredited Certification Body (CB) in cybersecurity. Siemens has opened its "Cyber Security Operation Center" (CSOC) for the protection of industrial facilities, with a joint location in Lisbon and Munich and one in Milford (Ohio) in the USA. Siemens industrial security specialists based at these sites monitor industrial facilities all around the world for cyber threats, warn companies in the event of security incidents and coordinate proactive countermeasures. These protective measures are part of Siemens' extensive Plant Security Services with which the enterprise supports companies in the manufacturing and processing industry in encountering constantly changing security threats and increasing plant availability.
Siemens has opened its "Cyber Security Operation Center" (CSOC) for the protection of industrial facilities, with a joint location in Lisbon and Munich and one in Milford (Ohio) in the USA. Siemens industrial security specialists based at these sites monitor industrial facilities all around the world for cyber threats, warn companies in the event of security incidents and coordinate proactive countermeasures. These protective measures are part of Siemens' extensive Plant Security Services with which the enterprise supports companies in the manufacturing and processing industry in encountering constantly changing security threats and increasing plant availability.